This Month in Security: August 2025 - Kerberos Zero-Day, Nx Supply Chain Compromise, and more


Title image, "Malware Infection" by Visual Content, is licensed under CC BY 2.0.
This month was highlighted by a publicly disclosed zero-day vulnerability in the Windows Kerberos protocol. This created patching urgency by defenders. We also saw a continued increase of significant data breaches stemming from third party and supply chain compromises.
Critical Zero-Day Exploits
August’s patch cycle was tense due to the pre-disclosure of a critical vulnerability in a core Windows authentication service.
- Kerberos Zero-Day (CVE-2025-53779): This Zero-day was publicly disclosed, but has not been actively exploited. The elevation of privileges flaw could allow attackers to gain domain administrator privileges, posing a risk to enterprise environments. Microsoft addressed this in their Patch Tuesday release cycle (CrowdStrike).
- Apple Zero-Day (CVE-2025-43300): Apple released emergency security updates to patch CVE-2025-43300 affecting iPhones, iPads, and Macs. The vulnerability could result in memory corruption if a malicious image was processed. There have been reports of this vulnerability being actively exploited against a targeted group of users, but that group has not been identified (TheHackerNews).
Notable Threats and Incidents
Third party breaches and sophisticated malware campaigns continued to cause disruption and data loss this month.
- Google and Workday Data Breach: Google confirmed that Salesforce, one of its third party vendors, exposed 2.55 million individuals business contact information. The attack was attributed to the ShinyHunters group. Shortly after the attack Workday disclosed it was also impacted by the same Salesforce compromise, exposing similar data (Bright Defence).
- MacOS Infostealer Campaign: MacOS was targeted by a malvertising campaign between June and August containing malicious ads in Google search results for software like Homebrew. This led users to fake websites that tricked them into executing commands to install the SHAMOS infostealer (Infosecurity Magazine).
- AWS Certificate Manager Data Exfiltration Discovered: A security researcher discovered a novel way to use AWS’s Certificate Manager (ACM) certificate import functionality to create a covert communication channel, allowing an attacker to transfer up to 2MB of data per request. It is particularly difficult to detect with standard tools, like CloudTrail (Constas Kou).
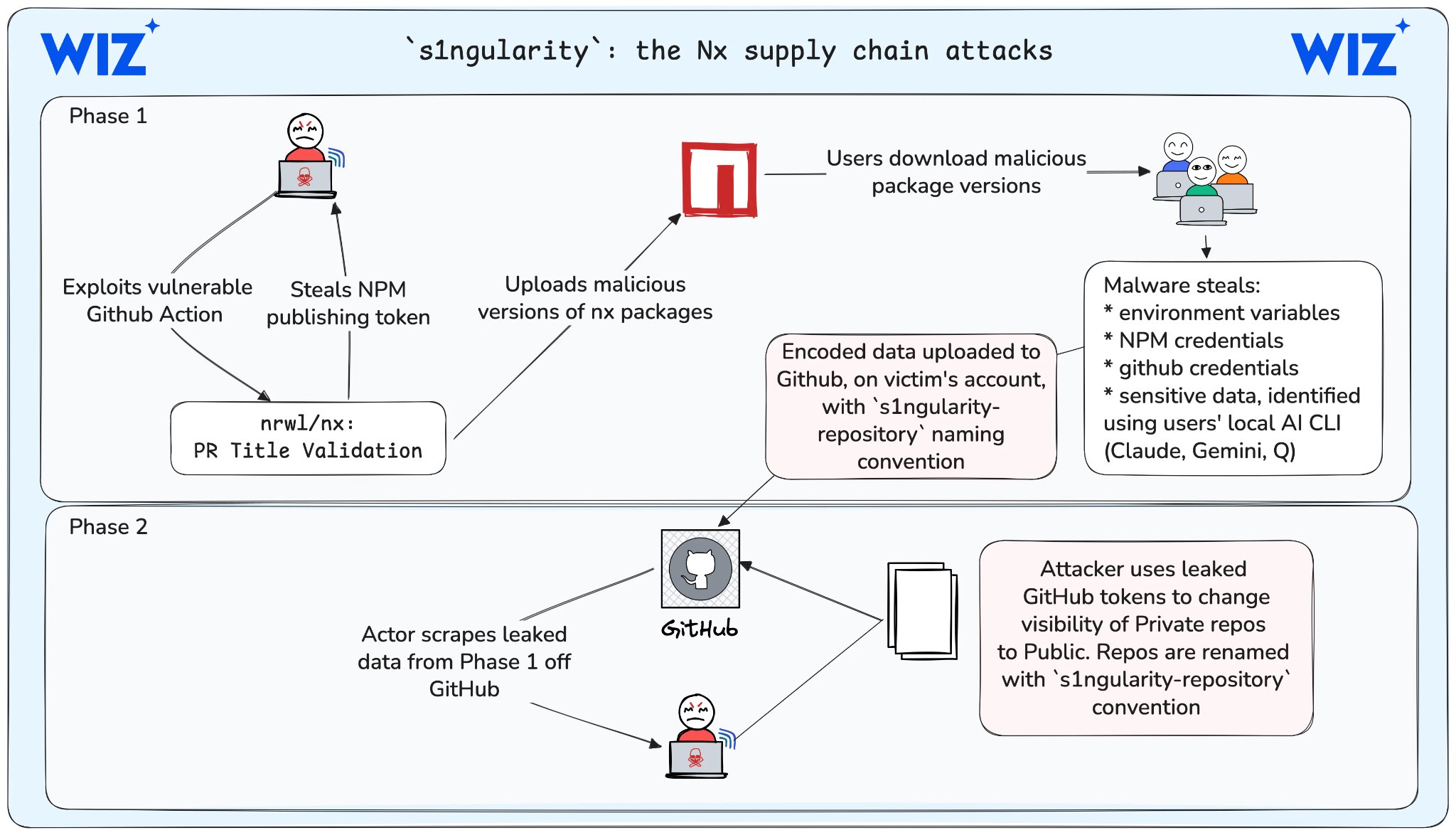
- Software Supply chain Attack Hits Nx Monorepo Tool: A major software supply chain attack was discovered involving the nx npm package. Nx is a widely used tool for managing large monorepos. Public repos prefixed “s1ngularity-repository” were added to affected GitHub accounts. These repos were created by a “malicious post-install command executed by the install of the nx build kit” (Semgrep). The malware was designed to steal cryptocurrency wallets and API keys. A detailed outline of the attack is pictured below from Wiz.
Policy and Framework Updates
Government agencies focused on security emerging technologies and providing guidance against common attack vectors.
- NIST Released “Ascon-Based Lightweight Cryptography Standards for Constrained Devices”: NIST published Special Publication 800-232, establishing the Ascon family of algorithms as the standard for lightweight cryptography. This is designed to provide strong but efficient security for resource-constrained devices, such as IoT devices (Digital Policy Alert).
- Federal Trade Commission (FTC) Warns Tech Giants on Encryption: The U.S. FTC issued a warning to major tech companies, stating that compliance with foreign government demands to weaken encryption or enabling censorship would violate U.S. consumer protection laws. They emphasized that their primary obligation is to protect American consumers data (FTC.gov)
August Patches and Vulnerabilities
August's Patch Tuesday addressed over 100 vulnerabilities, including several critical flaws and zero-days.
- Microsoft's August Patch Tuesday: On August 12th, Microsoft released patches for 111 vulnerabilities, including 13 critical vulnerabilities (SOCRadar).
- The update addressed the publicly disclosed Kerberos zero-day (CVE-2025-53779).
- Two severe RCE vulnerabilities in the Windows Graphics Component (CVE-2025-50165) and GDI+ (CVE-2025-53766) were included in the patches. Both vulnerabilities have a CVSS score of 9.8 and can be exploited via a malicious image file that does not require user interaction.
- Other critical patches addressed flaws in Windows NTLM, Microsoft Word, and Microsoft Message Queuing (MSMQ) (SOCRadar).
Key Takeaways for Staying Secure
- Prioritize Patching Critical Windows Flaws: CVE-2025-53779, CVE-2025-50165 and CVE-2025-53766 should be patched immediately to prevent potential domain wide compromises and remote attacks.
- Update All Apple Devices: The actively updated vulnerability Apple zero-day, CVE-2025-43300, affecting iPhones, iPads, and Macs should be patched as soon as possible to protect against the targeted attacks.
- Scrutinize Third Party Software: Breaches at Google, Workday, and the use of the nx package for malware underscore the critical need to audit both third party vendors and open source dependencies.
- Beware of Sophisticated Phishing and Malware Lures: Threat actors are using increasingly more sophisticated social engineering attacks. Take training to learn about these types of attacks and how to spot them.
- Reach Out: When needed, reach out to a trusted provider to review your security posture, like Cloud Security Partners.
Stay in the loop.
Subscribe for the latest in AI, Security, Cloud, and more—straight to your inbox.
